Backup and Restore PGP keys with Encrypted USB Flash Drive
This guide presumes you have completed the following steps:
- Generated your PGP Certify key.
- Noted the full 40-character fingerprint. Example: E108123456FB2280ABC123DAE24318EF3BABCDEF
Whenever [fingerprint] is mentioned in this guide, substitute it with your complete 40-character fingerprint.
This guide will demonstrate how to back up your GnuPG directory (which contains all PGP keys) by creating an encrypted USB flash drive partition.
Creating an encrypted USB flash drive
You must install the package called cryptsetup.
1
sudo apt install cryptsetup
Creating an encrypted partition is simple with tools like KDE Partition Manager or GNOME Disk Utility. This guide will demonstrate how to create an encrypted USB flash drive partition using KDE Partition Manager.
- Insert the flash drive into the system’s USB port. Determine the device name using
dmesgorlsblk. For this guide, we’ll assume it’s sda1. - Open the KDE Partition Manager from the applications menu. Enter the password when prompted. Identify the USB flash drive in the left panel and select it.
- If the device is mounted, unmount it by right-clicking on the partition (e.g., /dev/sda1) in the right panel and choosing “Unmount.”
- Delete the partition by right-clicking on it.
- Create a new partition via Menu -> Partition -> New. Select File system: ext4, check “Encrypt with LUKS,” and enter the encryption password. You may use the same password as the private key creation. Assign a label (e.g., SecureI) for an identifiable mount point. Click OK, then Apply.
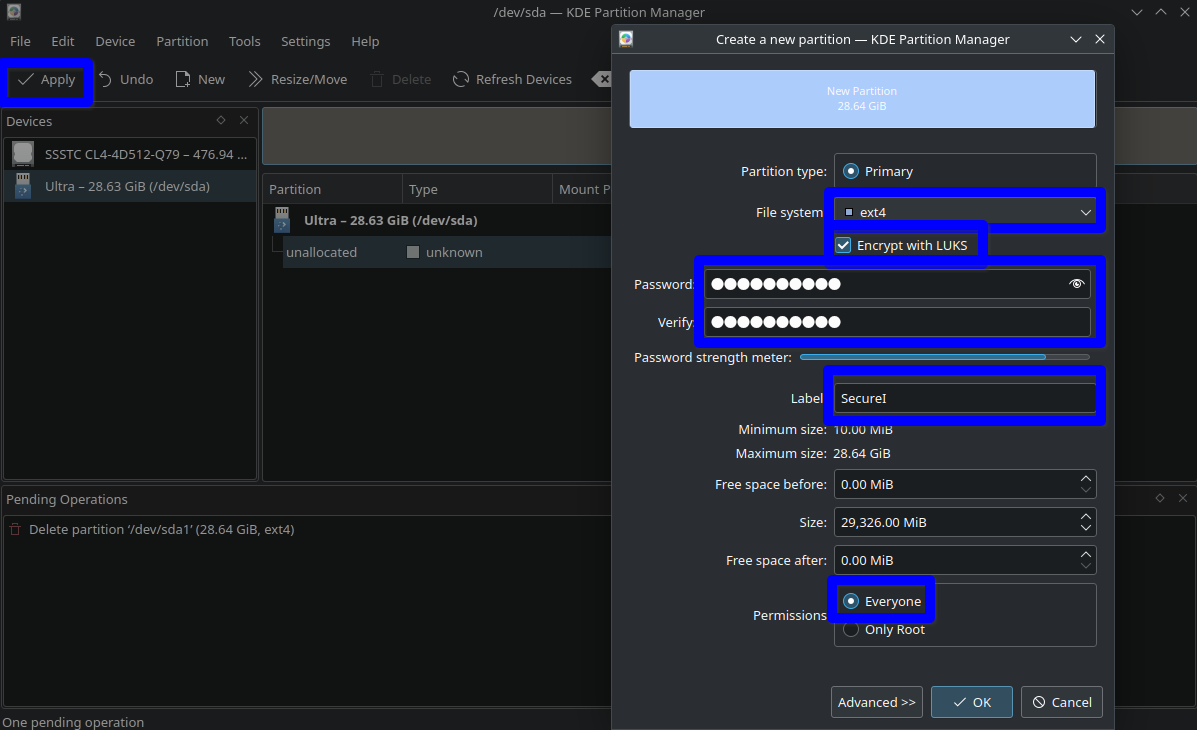 USB Flash Drive encryption using KDE Partition Manger
USB Flash Drive encryption using KDE Partition Manger
(Un)Mounting the encrypted flash drive
When you reinsert the encrypted USB drive into the USB port, it will prompt for the encryption password. After entering the password, the drive will be mounted to the specified mount point (e.g., SecureI) based on the label assigned in the above step.
Alternatively, here is a command-line method for mounting and unmounting the encrypted flash drive.
Commands to mount the flash drive
1
2
sudo cryptsetup luksOpen /dev/sda1 SecureI
sudo mount /dev/mapper/SecureI /media/$USER/SecureI
The first command creates a mapper device /dev/mapper/SecureI. You might need to enter two passwords: one for sudo and the other for encryption. The second command mounts the device to the mount point /media/$USER/SecureI if it is not already mounted.
Commands to unmount the flash drive
1
2
sudo umount /media/nayab/SecureI
sudo cryptsetup luksClose SecureI
Copy GnuPG directory to the flash drive
1
2
sudo chown -R $USER:$USER /media/$USER/SecureI
cp -r ~/.gnupg /media/nayab/SecureI/
Testing the backup
1
gpg --homedir=/media/nayab/SecureI/.gnupg/ --list-key [fingerprint]
If you don’t see any errors, you are good to go.
Restoring the GnuPG directory
1
2
rm -rf ~/.gnupg/
cp -r /media/nayab/SecureI/.gnupg ~/